In China. Beautiful
Wednesday, December 28, 2011
Monday, December 19, 2011
Free online education
A fairly comprehensive list of free, online courework and other educational resources
In addition to the existing MIT site listed, a new program, MITx, has just been announced.
In addition to the existing MIT site listed, a new program, MITx, has just been announced.
Friday, December 16, 2011
Clock of the Long Now
Good summary article on how the Clock of the Long Now works. This clock is designed to run for 10,000 and is being built in Texas.
Wednesday, December 7, 2011
NYTimes Computer Hisotry Timeline
Participatory timeline of the history and future of computing. Make predictions on what the future holds.
Timescape
We live on a pretty cool planet, and thankfully, there are talented people to capture the amazing images. A preview of Timescapes.
Sunday, December 4, 2011
The Internet of Things: Streaming Data
Pachube is a site that allows users to stream data to and collect data from the site in real time. Examples include sensors for radiation, temperature, and light level. Often, microcontrollers like the Arduino are used to collect and transmit data. The site offers are rich API along with online tools such as visualization and mapping. Not sure exactly what I could use it for, but seems interesting.
Wednesday, November 16, 2011
Santa Fe Institute short course
Something to follow up:
SFI short courses:
Santa Fe Institute's Short Course on Complexity: Exploring Complexity in Science and Technology September, 2012 San Francisco Bay Area
SFI short courses:
Santa Fe Institute's Short Course on Complexity: Exploring Complexity in Science and Technology September, 2012 San Francisco Bay Area
Sunday, November 13, 2011
Installing VMWareTools on Debian Lenny
Not officially supported, requires some tweaking of the version of gcc used.
For details, see the source from this blog.
Basic process, not annotated
apt-get install binutils cpp gcc make psmisc linux-headers-$(uname -r)
mount /dev/cdrom /mnt/
tar -C /tmp -zxvf /mnt/VMwareTools-x.x.x.tar.gz
umount /mnt
ln -sf /usr/bin/gcc-4.1 /usr/bin/gcc
cd /tmp/vmware-tools-distrib
./vmware-install.pl
ln -sf /usr/bin/gcc-4.3 /usr/bin/gcc
reboot
For details, see the source from this blog.
Thursday, November 10, 2011
Tuesday, November 8, 2011
From Difference Engine to Analytical Engine
 |
| Modern build of the Difference Engine |
The New York Times is reporting that a project is underway to build Babbage's Analytical Engine. The Analytical Engine was supposed to be a general purpose, programmable computer. Unlike the Difference Engine, plans for this machine are not complete. That, however, didn't stop Ada Lovelace from 'programming' this computer, winning her the title of world's first computer programmer.
 |
| Plan for part of the Analytical Engine |
 |
| partial mock-up of Analytical Engine |
Sunday, November 6, 2011
Watch Porn: Exploding Time
Harry Winston and Denis Giguet partner to make one of the most unique (and expensive) watches. Words can't really describe it, so here is the vid:
The designer, Denis Giguet explains and demonstrates the watch here:
With over 500 parts, 166 jewels, and a price tag of around a quarter of a million, I'll have to live with just the videos. Full details here
The designer, Denis Giguet explains and demonstrates the watch here:
With over 500 parts, 166 jewels, and a price tag of around a quarter of a million, I'll have to live with just the videos. Full details here
Friday, November 4, 2011
Glass Steam Engine
Great video of an all-glass steam engine. No seals were used- just well fitting glass.
Wednesday, November 2, 2011
SSH auto login, no password, with security
Title is a mouth full, but very important.
SSH allows one to generate a public/private key pair and use them for logging in without a password. Very convenient. However, most people do this in an insecure way, by using a blank passphrase on the private key. If you set a pass phrase on the private key, then every time you use it to login to a remote machine, you'll need to enter it, which defeats the utility of key based authentication.
A three part article by IBM goes into the details of how SSH works, and how to use public key authentication while still maintaining the security of your private key.
Its a bit involved, but definitely worth a read.
SSH allows one to generate a public/private key pair and use them for logging in without a password. Very convenient. However, most people do this in an insecure way, by using a blank passphrase on the private key. If you set a pass phrase on the private key, then every time you use it to login to a remote machine, you'll need to enter it, which defeats the utility of key based authentication.
A three part article by IBM goes into the details of how SSH works, and how to use public key authentication while still maintaining the security of your private key.
Its a bit involved, but definitely worth a read.
Moore's Law: From this to that with an ENIAC
The ENIAC is considered the first general purpose, programmable, Turing-complete computer. It was, quite literally, the size of a room:
For the machine's 50th anniversary, folks at the University of Pennsylvania implemented the entire machine on a single chip:
This chip is on display at the Computer History Museum in Mountain View, CA.
For the machine's 50th anniversary, folks at the University of Pennsylvania implemented the entire machine on a single chip:
This chip is on display at the Computer History Museum in Mountain View, CA.
Thursday, October 20, 2011
Shot now, focus later.
Silicon Valley star-up Lytro is releasing a new kind of camera that will change the way pictures are taken: the company is calling it 'light-field' technology. Rather than focus the image on a standard sensor, this technology also records the angle of the light which allows the picture to be refocus after the fact.
Its a little oddly shaped and has very few controls: on/off, shutter, and zoom. The memory is fixed (no SD card).
An example of what you can do with this technology:
Same picture, different subject is put in focus. With a regular camera, this would be two different pictures (good luck getting BOTH cats to stay in the same location).
The company has a photo gallery, with some of the pictures you can change the focus on. There is a picture of a Nixue Tube clock
Here are a couple of articles:
Technology Review
CNet
Its a little oddly shaped and has very few controls: on/off, shutter, and zoom. The memory is fixed (no SD card).
An example of what you can do with this technology:
Same picture, different subject is put in focus. With a regular camera, this would be two different pictures (good luck getting BOTH cats to stay in the same location).
The company has a photo gallery, with some of the pictures you can change the focus on. There is a picture of a Nixue Tube clock
Here are a couple of articles:
Technology Review
CNet
Monday, October 17, 2011
Science, Magic, and Religion
File under: things to do if I had more time:
History 2D from UCLA, Science, Magic, and Religion is online.
Eighteen hour long lectures.
History 2D from UCLA, Science, Magic, and Religion is online.
Eighteen hour long lectures.
Sunday, October 9, 2011
Why the UN should never be involved with the Internet
Underscoring and providing yet more evidence that the United Nations should have no role in Internet governance, the General of the UN's World Intellectual Property Organization (WIPO) says that the Internet would be a better place if it was patented and controlled. BoingBoing has the sad story.
Thursday, October 6, 2011
Copyright / Patent trolls - its the zombie apocalypse
Sad news on the "information wants to be free" front. Time zone data may not be the most sexy thing, and probably is something most people don't ever think about, but there is a data base of worldwide timezeons.
The full story is on Stephen Colebourne's blog.
The short story is that a company called Astrolabe has filed suit against the open source timezone project claiming copyright infringement.
First off, I didn't know you could copyright facts (see 1st question), but what is really insulting is that this company offers free products: a free birth chart (aka horoscope).
Really?
The full story is on Stephen Colebourne's blog.
The short story is that a company called Astrolabe has filed suit against the open source timezone project claiming copyright infringement.
First off, I didn't know you could copyright facts (see 1st question), but what is really insulting is that this company offers free products: a free birth chart (aka horoscope).
Really?
Monday, October 3, 2011
Two video editors
I don't normally deal with video much, partly because of the lack of software, but here are two free/open source editors:

VLMC from the creators of VLC, the Swiss army knife of a media player, has been in alpha (0.10) release for quite a while. Looks powerful, yet simple, but unfortunately, is still a bit unstable.
Just found out about Lightworks. Its a public beta, Windows only. Haven't downloaded it yet.

VLMC from the creators of VLC, the Swiss army knife of a media player, has been in alpha (0.10) release for quite a while. Looks powerful, yet simple, but unfortunately, is still a bit unstable.
Just found out about Lightworks. Its a public beta, Windows only. Haven't downloaded it yet.
Friday, September 30, 2011
Calling toll free numbers for free (the SIP way)
Of course calling a toll free number should be free. But what if you have to pay to make any call, say, on your cell phone (you're using minutes), in a hotel, or overseas (yes, you can call US toll free numbers from overseas, but you still have to pay the going rate for calls to the US). There are many companies that offer toll free call origination over SIP, no registration or contract required.
This can be setup in a corporate PBX, or even straight from a client on your laptop.
Here's an example. Using SJPhone you can place calls to SIP URIs (Uniform Resource Identifier). SIP is a peer-to-peer protocol, meaning, your SIP client can send SIP messages to another SIP client without having to register or authenticate if the other side doesn't require such things. Generally, this is an uncommon situation. However, in this case, some companies are providing this service for free, there is no need to setup an account.
In this case, we are using Denetron. In order to place a call, in the address bar of the phone, put the following:
sip:tollfreenumber@sip.denetron.com
The toll free number for this service must be in the 11-digit format (1-800, 1-888, etc).
This is what the client will look like
The client should be in the PC to PC (SIP) mode or profile.
This would be useful if you are overseas and trying to reach a US toll free number. You can now do it for free. Or, if you are in a place where your cell phone doesn't work, but you have a network connection.
A few services I've tried so far:
Denetron: sip:1800NXXXXXX@sip.denetron.com
IdeaSIP : sip:800NXXXXXX@proxy.ideasip.com
TollFreeGateway.com: sip:800NXXXXXX@sip.tollfreegateway.com
TollFreeTollFree.com: sip:800NXXXXXX@tollfreetollfree.com
In these examples, '800' is used to represent all NPAs for toll free calls, including 800,888, 866, 877....
Other services I haven't yet tried:
Call with us: sip: 1800NXXXXXX@tf.callwithus.com
This can be setup in a corporate PBX, or even straight from a client on your laptop.
Here's an example. Using SJPhone you can place calls to SIP URIs (Uniform Resource Identifier). SIP is a peer-to-peer protocol, meaning, your SIP client can send SIP messages to another SIP client without having to register or authenticate if the other side doesn't require such things. Generally, this is an uncommon situation. However, in this case, some companies are providing this service for free, there is no need to setup an account.
In this case, we are using Denetron. In order to place a call, in the address bar of the phone, put the following:
sip:tollfreenumber@sip.denetron.com
The toll free number for this service must be in the 11-digit format (1-800, 1-888, etc).
This is what the client will look like
The client should be in the PC to PC (SIP) mode or profile.
This would be useful if you are overseas and trying to reach a US toll free number. You can now do it for free. Or, if you are in a place where your cell phone doesn't work, but you have a network connection.
A few services I've tried so far:
Denetron: sip:1800NXXXXXX@sip.denetron.com
IdeaSIP : sip:800NXXXXXX@proxy.ideasip.com
TollFreeGateway.com: sip:800NXXXXXX@sip.tollfreegateway.com
TollFreeTollFree.com: sip:800NXXXXXX@tollfreetollfree.com
In these examples, '800' is used to represent all NPAs for toll free calls, including 800,888, 866, 877....
Other services I haven't yet tried:
Call with us: sip: 1800NXXXXXX@tf.callwithus.com
IBM's brain chip
BBC is reporting that IBM has made a processor that acts like the human brain. Maybe this can be combined with the Eye Camera
Thursday, September 22, 2011
Electronics Shopping in Asia
Two places I would love to visit for browsing and buying electronics:
SEG Electronics Market in Shenzhen, Guangdong, China
Akihabara in Tokyo
SEG Electronics Market in Shenzhen, Guangdong, China
Akihabara in Tokyo
The U.S. Army Corps of Engineers in the Development of Washington, D.C., 1790-2004
Haven't looked through the whole thing yet, but this book looks interesting
Wednesday, September 21, 2011
Arduino, even simpler?
Arduino is an open source microcontroller for learning electronics and prototyping projects. It seems someone has taken it a step further, abstracted some of the complexity of coding, and made learning even simpler. Teagueduino is still in the beginning stages, but it looks really interesting.
Tuesday, September 20, 2011
Sunday, September 11, 2011
Saturday, September 10, 2011
The future of interactive communications on the Internet
Good interview with Andy Ory, new CEO of Acme Packet concerning the future of interactive communication (think voice and video) on the internet. Some interesting quotes:
The notion of bandwidth being unlimited is a myth. And the notion of all communications being of equal importance is a myth. Some sessions are just more important than others. The Internet, the Layer 3 network, doesn't think from a session point of view, it thinks from a packet point of view. It isn't able to recognize and make these kinds of deterministic decisions that need to be made for people to really feel comfortable that the network's meeting their global need. So that's another example of what you get out of your telephone network that you don't get out of your Internet.
What I am saying is that applications and services are going to emerge that allow us to federate our economic and social lives in a way where we can control who can reach us, when, how and under what circumstances. That is a major, major change.
You don't want to [call into a contact center] because it takes time and nobody ever hangs up as a customer from a contact center and says, wow, I'm really glad I made that call.
Sunday, August 28, 2011
File Under: things to read: Data Visualization Blog
Fell In Love With Data. I've gotten interested in all sorts of different data visualizations lately, but haven't really figured out how to get started. Maybe this blog is just the thing. The proposed outline looks promising:
Andy Kirk over at Visualizing Data is planning on offering 1 day training courses in the US hopefully in 2012.
Here is a tentative list of topics I am planning to cover in the series (subject to changes):
- Books and Other Resources
- Programming Languages and Tools
- Sources of Good Examples
- Research Papers
- University Courses
Andy Kirk over at Visualizing Data is planning on offering 1 day training courses in the US hopefully in 2012.
Friday, August 26, 2011
Thursday, August 18, 2011
File Under: things to buy
An SD HC card that has an integrated USB connector. Useful for those times when you don't have a USB cable for your camera.
SanDisk has a similar product: Sandisk Ducati
SanDisk has a similar product: Sandisk Ducati
Wednesday, August 17, 2011
Packet Analysis in the Cloud
So, aside from resisting anything with 'cloud' in the title, I've avoided "cloud" based packet analysis tools because they didn't make sense to me. Packet capture an analysis is very much a local thing. Usually, you need to be attached to a device to capture packets. Even with technologies like RSPAN and ERSPAN, packets always end up on a machine, are analyzed, and then forgotten.
Its the forgotten part that is the problem. For a long time I've wanted to created a shared library for reference packet captures- a view of what things should look like when they're working. It appears someone not only had that idea, but the ability to create a product around it: CloudShark. Software or hardware appliance that stores packet captures for sharing and annotation.
There is also pcapr which seems to provide many of the same features, and even more, though I haven't done a full comparison of the two.
Its the forgotten part that is the problem. For a long time I've wanted to created a shared library for reference packet captures- a view of what things should look like when they're working. It appears someone not only had that idea, but the ability to create a product around it: CloudShark. Software or hardware appliance that stores packet captures for sharing and annotation.
There is also pcapr which seems to provide many of the same features, and even more, though I haven't done a full comparison of the two.
Wednesday, August 10, 2011
When bad things happen to good fiber
VP from Level3 recounts strange things that have happened to its fiber over the years.
Sunday, August 7, 2011
Toward copyright sanity (in the UK)
Ars Technica has an article about copyright reform in the UK. From the article:
The British government today pledged (PDF) to enact significant changes to copyright law, including orphan works reforms and the introduction of new copyright exceptions. And the tone of the comments was surprising: the government agrees that "copyright currently over-regulates to the detriment of the UK." CD (and perhaps DVD) ripping for personal use should become legal at last—and the government is even keen to see that the consumer rights granted by law can't simply be taken away by contract (such as a "EULA" sticker on a CD demanding that a disk not be ripped).
Friday, August 5, 2011
You Are My Sunshine
Thursday, August 4, 2011
Internet Topology Zoo
The University of Adelaide has an interesting site: The Internet Topology Zoo. Its a collection of visualizations, tools, and data sets for visualizing internet service providers. These visualizations have been all gussied up- by properly placing nodes on maps, but other data sets used in tools such as Cytoscape or Gephi will not only visualize but analyze large networks.
I would love to recreate the snapshot of the internet created by M. Newman in May 2006 with current data to determine such metrics as closeness or betweeness of GW's autonomous system.
I would love to recreate the snapshot of the internet created by M. Newman in May 2006 with current data to determine such metrics as closeness or betweeness of GW's autonomous system.
Monday, August 1, 2011
Wireless with lights
There are a couple of initiatives to provide local wireless data connectivity with lighting. Here is one example.
Ultrafine positioning
Technology Review reports on a new Australian company, Locata, developing a new augmentation to GPS for ultrafine positioning.
By deploying earth based transmitters that work along side the GPS signal, ultrafine positioning can be obtained. There are very few details on how this works, such as number of transmitters, frequency, power, etc. How does this compare with other GPS helpers such as WAAS or dGPS?
A while back there was a proposal to use television frequencies (which have much better propagation properties) to provide indoor positioning. I can no longer find any references to this project. I believe it was envisioned by a guy name Rosen, who was involved with the original GPS system.
By deploying earth based transmitters that work along side the GPS signal, ultrafine positioning can be obtained. There are very few details on how this works, such as number of transmitters, frequency, power, etc. How does this compare with other GPS helpers such as WAAS or dGPS?
A while back there was a proposal to use television frequencies (which have much better propagation properties) to provide indoor positioning. I can no longer find any references to this project. I believe it was envisioned by a guy name Rosen, who was involved with the original GPS system.
Friday, July 29, 2011
Book: First Rate Madness
Are good leaders mentally ill? Interesting book considers the hypothesis:
In times of crisis, [Nassir Ghaemi] concludes, "we are better off being led by mentally ill leaders than by mentally normal ones".
Thursday, July 28, 2011
Friday, July 22, 2011
Wednesday, July 20, 2011
The God complex & politicians
TED has an important talk from Tim Harford: Trial, error and the God Complex.
Over simplifying, the God complex is the belief that we can know everything about complex systems,
This is an important concept to keep in mind when listening to politicians drop sound bites and one liners. For example, a typical party line is that lowering taxes (always) creates jobs. There is logic to this statement, and I would generally agree that lower taxes are better than higher taxes. But, the tax code is too complex for one person to fully understand. Combined with the amazingly complex system of "the economy," I don't believe it is possible to make such broad (and often times) absolute statements like "doing X always leads to action Y"
Over simplifying, the God complex is the belief that we can know everything about complex systems,
This is an important concept to keep in mind when listening to politicians drop sound bites and one liners. For example, a typical party line is that lowering taxes (always) creates jobs. There is logic to this statement, and I would generally agree that lower taxes are better than higher taxes. But, the tax code is too complex for one person to fully understand. Combined with the amazingly complex system of "the economy," I don't believe it is possible to make such broad (and often times) absolute statements like "doing X always leads to action Y"
Tuesday, July 19, 2011
Equal Time for Creationism
A common argument for teaching Intelligent Design creationism is to teach it along side evolution and let the kids decide. There isn't enough evidence for either one, so lets teach both.
Why stop at evolution. There are other areas that have alternate theories:
Why stop at evolution. There are other areas that have alternate theories:
Thursday, July 14, 2011
Tuesday, July 12, 2011
Can Monkeys own copyrights?
Seems that a monkey was using an idle camera to take self portraits:
So, when websites started using the images, you can imagine what happened. The Carter News Agency is asking sites to remove the images. The justification: TechDirt doesn't own the copyright.
Question is: who does. If no one, then what authority does Carter have in asking TechDirt to remove the images. Does the request imply that Carter think that it owns the copyrights? If so, how. If not, then the request is baseless. In fact, making false DMCA take down claims (which has not (yet) happened) is itself illegal.
So, when websites started using the images, you can imagine what happened. The Carter News Agency is asking sites to remove the images. The justification: TechDirt doesn't own the copyright.
Question is: who does. If no one, then what authority does Carter have in asking TechDirt to remove the images. Does the request imply that Carter think that it owns the copyrights? If so, how. If not, then the request is baseless. In fact, making false DMCA take down claims (which has not (yet) happened) is itself illegal.
Monday, July 11, 2011
Stuxnet: the long story
Wired has a great piece on the Stuxnet virus that targeted the uranium enrichment facility at Ntanz, Iran.
Watch Porn: Thomas Prescher Triple Axis Tourbillon Regulator
In this case, watch is a noun, not verb
Thomas Prescher Triple Axis Tourbillon Regulator
Check out the video
Thomas Prescher Triple Axis Tourbillon Regulator
Check out the video
Sunday, July 10, 2011
.secure domain...first thoughts
Some in the federal government are talking about creating a new top level domain: .secure
Access to this domain might require validated digital credentials and provide services for banking and critical infrastructure, but might also require voluntarily giving up Fourth Amendment rights (read: deep packet inspection, lack of anonymity).
Perhaps this is a better options than the Internet Kill Switch?
Access to this domain might require validated digital credentials and provide services for banking and critical infrastructure, but might also require voluntarily giving up Fourth Amendment rights (read: deep packet inspection, lack of anonymity).
Perhaps this is a better options than the Internet Kill Switch?
Copyright Cartel: "Child pornography is great"
While Torrent Freakmay not be the most neutral reporter of news, this article is beyond belief. (well, given the source of the quote, I guess it is believable).
In short, the copyright cartel (this time in Europe) is trying to associate child pornography with peer-to-peer file sharing in an effort get lawmakers to pass legislation controlling what we do online.
Nice business these guys are in.
In short, the copyright cartel (this time in Europe) is trying to associate child pornography with peer-to-peer file sharing in an effort get lawmakers to pass legislation controlling what we do online.
Nice business these guys are in.
Saturday, July 9, 2011
Wireless power
Tesla technology coming to life: pulling power out of the ether. This technology may not provide power as Tesla had imaged, but it is impressive nonetheless. The technology has the potential to capture up to a couple of milliwatts from RF broadcasts (radio, TV, radar, etc). Combine this with other power generation/collection (such as solar or small scale wind) and a good storage technology (supercapacitor) and this might be a way to provide power small sensors. Imagine having thousands of weather sensors providing massive widescale weather information. Maybe this could improve weather forecasts?
Now, if we could only increase the current power available over electricity over glass, my life would be easier.
Now, if we could only increase the current power available over electricity over glass, my life would be easier.
Friday, July 8, 2011
ISPs and the copyright cartel collude to monitor your traffic
After many years of negotiation, the ISPs have finally caved into the copyright cartel and established something innocuously called the "Copyright Alert System." This will notify consumers of accusations of copyright infringement.
Without any due process, you can be accused of, and potential have your service suspended because of, accusations of copyright infringement. If you cry foul, you'll have to pay for an independent review.
This is called extortion.
Without any due process, you can be accused of, and potential have your service suspended because of, accusations of copyright infringement. If you cry foul, you'll have to pay for an independent review.
This is called extortion.
Thursday, July 7, 2011
Up against a ceiling
While it's obvious the debt ceiling must be lifted, I can't help but stop in awe at the succinct wisdom of our first president:
Allowing Congress to continuously raise the debt ceiling is like allowing a college kid to set his own credit limit.
But what is the alternative?
To contract new debts is not the way to pay old ones.
GEORGE WASHINGTON, letter to James Welch, Apr. 7, 1799
Allowing Congress to continuously raise the debt ceiling is like allowing a college kid to set his own credit limit.
But what is the alternative?
On political parties
John Adams on political parties:
There is nothing which I dread so much as a division of the republic into two great parties, each arranged under its leader, and concerting measures in opposition to each other. This, in my humble apprehension, is to be dreaded as the greatest political evil under our Constitution.A sentiment that George Washington shared in his farewell address:
However [political parties] may now and then answer popular ends, they are likely in the course of time and things, to become potent engines, by which cunning, ambitious, and unprincipled men will be enabled to subvert the power of the people and to usurp for themselves the reins of government, destroying afterwards the very engines which have lifted them to unjust dominion.
Places I'd like to vist I : Paro Taktsang
Beautiful picture of Paro Taktsang, a Buddhist temple in Bhuta.
Is the sky really falling this time?
Disconcerting article from Market watch....Age of America Nears End. The IMF is estimating that China's share of world GDP will surpass that of the US by 2016.
Previously, in the late 80s, the big scare was that Japan would surpass the US. But, the Lost Decade may have killed that prediction.
Previously, in the late 80s, the big scare was that Japan would surpass the US. But, the Lost Decade may have killed that prediction.
Thursday, June 30, 2011
Fineo
Fineo is an interesting tool to help visualize categorical data. Using simple tab-separated-values file, you can create diagrams that allow users to select the categories to explore the relationships between and among them.
A sample diagram is here.
A sample diagram is here.
Wednesday, June 29, 2011
The (sad) state of broadband in the US
Engadget has an excellent article on why the state of US broadband is poor compared to other developed contries. The video along with the article is definitely worth watching. While I wont summarize the entire article here, there are some key points:
In the European countries highlighted in the video, the governments have forced the incumbent local providers to allow competitors to use the last mile loops going to each home.
Of course, Verizon and AT&T think this is a horrible idea (except when it benefits them by allowing access to the European markets where they have no last mile infrastructure).
Maybe it is time to consider dedicating last mile infrastructure to a quasi-governmental authority like water and in some cases power. But, in a way, isn't that what we've done by granting (and in many cases maintaining) monopoly status to the duopoly?
- Prices in the US are higher and speeds are lower
- Most US markets are served by a duopoly (telco & cable TV company)
- Government has a roll in encouraging competition by opening up the last mile
In the European countries highlighted in the video, the governments have forced the incumbent local providers to allow competitors to use the last mile loops going to each home.
Of course, Verizon and AT&T think this is a horrible idea (except when it benefits them by allowing access to the European markets where they have no last mile infrastructure).
Maybe it is time to consider dedicating last mile infrastructure to a quasi-governmental authority like water and in some cases power. But, in a way, isn't that what we've done by granting (and in many cases maintaining) monopoly status to the duopoly?
Tuesday, June 28, 2011
(Nearly) Useless Trivia: IEEE naming convention
IEEE standards often have strange names such as 802.1ah. Ever consider there was a difference between standards that have lowercase trailing letters as opposed to uppercase? Well, there is a diffreence:
The IEEE project naming convention uses upper-case letters (eg: 802.1Q) to identify standalone standards, and lower-case letters to identify amendments (previously known as supplements) to existing standards. There should never be 2 projects differing only in the case of letters!Taken from itcertnotes.
EAT MORE CANDY
The candy industry just got a boost from an unlikely source. Turns out kids who eat candy are less likely to be overweight than their prudish friends.
Time to hit the candy store.
Time to hit the candy store.
Network Virtualization
Elsewhere on the switching front: virtualizing the network.
Nicira -- looks interesting, not much info on the website. Something to keep track of
Nicira -- looks interesting, not much info on the website. Something to keep track of
What happens when networks go open source
For a long time (well, probably since forever), software that runs networks was tightly coupled to the hardware on which it ran. For example, from Cisco, we have CatOS or IOS which has specific versions for specific platforms, leading to an explosion in the number of software images that customers needed to manage. Other vendors tamed the sprawl, mostly by having a single software image share by the entire product line (this was helped, of course, by the fact that not everyone can follow Cisco's growth model of acquisition).
But what if switching and routing software was decouple from the hardware. And what if that software was open source. Two projects to make note of: OpenFlow and Pica8
Switch++ looks similar, but probably not open source.
I haven't had a chance to play with either of these....maybe one day.
But what if switching and routing software was decouple from the hardware. And what if that software was open source. Two projects to make note of: OpenFlow and Pica8
Switch++ looks similar, but probably not open source.
I haven't had a chance to play with either of these....maybe one day.
Friday, June 24, 2011
Three Articles from the forefront of Your Rights Eroding
Three articles from both the United States and Australia discuss how ISPs are either filtering content or working with private copyright holders to throttle or block traffic just based on an accusation of copyright infringement.
Ars is reporting that the MPAA & RIAA areworking with colluding with large ISPs to throttle or limit access to users accused of copyright infringement. CNet is reporting the same story. Both explain how the White House is behind this effort to trash the Fourth, Fifth, and Sixth amendments.
News from Australia isn't any better: ISPs will start to voluntarily filter traffic based on a list provided by the Australian Communications and Media Authority.
When governments start filtering the information we can access and/or encourage private industry to restrict our access, we need to think about alternate means of communication such as TOR and Project Kleinrock
Ars is reporting that the MPAA & RIAA are
News from Australia isn't any better: ISPs will start to voluntarily filter traffic based on a list provided by the Australian Communications and Media Authority.
When governments start filtering the information we can access and/or encourage private industry to restrict our access, we need to think about alternate means of communication such as TOR and Project Kleinrock
Monday, June 20, 2011
Networking in the Apocolypse
We all should be creating disaster kits in case the unthinkable happens....flood, tornado, earthquake. But what about communication. What should you have? A solar charger, extra batteries? Sure.
But if the shit really hits the fan, how about a Kleinrock router. In short, it creates a web of wireless routers in repeater mode. Of course, content would either need to be hosted on this network or available through some gateway to the 'real' Internet.
But if the shit really hits the fan, how about a Kleinrock router. In short, it creates a web of wireless routers in repeater mode. Of course, content would either need to be hosted on this network or available through some gateway to the 'real' Internet.
Thursday, June 16, 2011
WiscNet is dead: Long Live the Bell Telephone Monopoly
Techdirt is reporting that WiscNet is dead because AT&T was able to get language inserted into legislation effectively killing this higher education and community resource.
Monday, June 13, 2011
A litany of disinachting news and articles
Oh, where to begin?
The University of Wisconsin's WiscNet is under attack from corporate service providers. According to the Ars Technica article, the Wisconsin State Telecommunications Association is working legislation through the state house that would force UW to return millions in stimulus money:
However, a federal law being proposed now, PROTECT IP, if passed, is likely to drastically change the land scape of higher education networks. In short, the act will be onerous burdens on network operators to protect and safeguard the intellectual property rights of copyright owners. Sounds like a great effort, but in reality, the RIAA and MPAA are shifting the cost of copyright protection from their for-profit members to network operators, all under the assumptions that network traffic is likely to infringe on a copyright.
Along the same lines, the MPAA and RIAA want to give police the power the search without a warrant for potentially illegal optical disc manufacturing facilities. Again, protecting copyrights is all well and good, but is it so important that we are going to make it easier for the government to infringe on our fourth amendment rights?
As it is, the FBI is lowering the bar for search and surveillance: giving them:
On a slightly different note, Tennessee has just made it illegal to post offensive images. The upside is that maybe this would make Weinergate illegal?
Good news all around. Maybe time to listen to some Joy Division.
The University of Wisconsin's WiscNet is under attack from corporate service providers. According to the Ars Technica article, the Wisconsin State Telecommunications Association is working legislation through the state house that would force UW to return millions in stimulus money:
Under a proposed new law, the University of Wisconsin system could be forced to return millions of dollars in federal broadband grants that it has already won, spend far more money on network services, and perhaps even withdraw from the Internet2 project.Universities have traditionally been strong proponents of open and free access to information resources, often partnering with communities and K-12 institutions to ensure low cost internet access.
However, a federal law being proposed now, PROTECT IP, if passed, is likely to drastically change the land scape of higher education networks. In short, the act will be onerous burdens on network operators to protect and safeguard the intellectual property rights of copyright owners. Sounds like a great effort, but in reality, the RIAA and MPAA are shifting the cost of copyright protection from their for-profit members to network operators, all under the assumptions that network traffic is likely to infringe on a copyright.
Along the same lines, the MPAA and RIAA want to give police the power the search without a warrant for potentially illegal optical disc manufacturing facilities. Again, protecting copyrights is all well and good, but is it so important that we are going to make it easier for the government to infringe on our fourth amendment rights?
As it is, the FBI is lowering the bar for search and surveillance: giving them:
more leeway to search databases, go through household trash or use surveillance teams to scrutinize the lives of people who have attracted their attention.To put another way, it will be easier for agents to work without an formal, open investigation which means less of a paper trail and less supervision, setting up a system that is more vulnerable to abuse.
On a slightly different note, Tennessee has just made it illegal to post offensive images. The upside is that maybe this would make Weinergate illegal?
Good news all around. Maybe time to listen to some Joy Division.
Where do we explore in space
Cool infographic showing the scope of human space exploration.
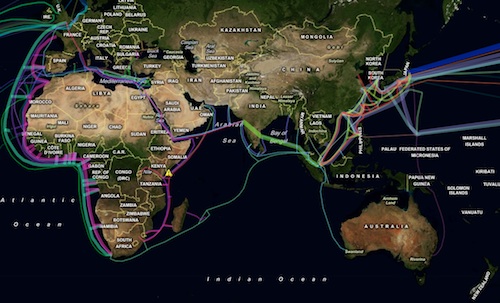
The 'Internet in 1901'
Undersea cable map from 1901.
Thursday, June 9, 2011
Write once, run everywhere?
Wasn't one of the main goals of Java the ability to write once, run everywhere? Good luck trying to run different Java applications on the same machine. I can't imagine a worse technology when it comes to maintaining backwards compatibility, which forces users to maintain multiple versions of Java.
Could Blue Stacks be the solution?
From the Technology Review Article about BlueStacks:
Could Blue Stacks be the solution?
From the Technology Review Article about BlueStacks:
A startup called BlueStacks wants to end all your worrying about whether an app will run on a specific operating system. The company's technology, which it's showing off at trade shows, lets users run apps on operating systems they weren't designed for.
The software lets Android apps run on Windows, and lets Android apps run within the browser on Google's ChromeOS. It can run Windows on top of Android or vice versa. The company will make the software available for download, but it can also be built into apps, and will come preinstalled on some hardware. "We don't care about the operating system anymore," says BlueStacks CEO Rosen Sharma. "It's all about apps."
Wednesday, June 8, 2011
Phase Change Memory
Still in development, better than NAND flash, Phase Change Memory looks really cool.
Pronto Systems
Pronto Systems is offering a super low cost 48x1G + 4x10G ethernet switch. What is really interesting is Pronto's involvement in the Open Switch Software Alliance:
There is OpenFlow which can be described as an API for programming switches' data planes directly.
There is also the (seemingly similar) Open Networking Foundation, a consortium of large network operators created to develop a software defined network.
Brad Hedlund has a good discussion on what problems Open Flow is trying to solve and if they are even valid.
OSSA is Open Switch Software Architecture which aims to provide an open software environment to increase the flexibility and manageability of data centers. OSSA includes three system layers, including boot loader, operating system, and software application.There is a lot of interesting working going on the the relatively boring ethternet switching space.
There is OpenFlow which can be described as an API for programming switches' data planes directly.
There is also the (seemingly similar) Open Networking Foundation, a consortium of large network operators created to develop a software defined network.
Brad Hedlund has a good discussion on what problems Open Flow is trying to solve and if they are even valid.
Wednesday, May 25, 2011
Your Rights: Eroding
Want to share negative opinions about a healthcare professional? Think again.
After the usual patient information form, there was a "mutual privacy agreement" that asked me to transfer ownership of any public commentary I might write in the future to Dr. CirkaTranslation: If you write a bad review about me, I'm going to claim ownership of it and delete it.
Tuesday, May 24, 2011
A new job for Chuck
Maybe Chuck can get a new job installing fiber in New England.
Actually, now is a good time to promote Chuck's blog: chuckbag. Lots of good stuff.
And seeing he's the only person reading this blog, I hope his loop detection mechanism is working
Actually, now is a good time to promote Chuck's blog: chuckbag. Lots of good stuff.
And seeing he's the only person reading this blog, I hope his loop detection mechanism is working
Saturday, May 21, 2011
Thunderbolt, round II: Apple, not Intel, files for trademark
Engadet reports an interesting development with Thunderbolt: Apple has filed for trademarks for the name, not its key developer Intel. Ultimately, this is likely to lead to more fragmentation of the peripheral connection space. Didn't Apple learn from the IEEE1394, iLink, Firewire naming confusion?
Friday, May 20, 2011
USB killed the Thunderbolt star
Extremetech has a good review of why Thunderbolt has already failed and why we shouldn't blindly listen to what Apple says.
Your Rights Eroding
Troubling news from California, where state legislators are set to allow warrentless searches and seizures to protect copyright holders. Both the RIAA and MPAA are obviously in favor of expanding the powers of law enforcement to protect their intellectual property and income, but one would hope that elected representatives would be looking out for citizens and the Constitution.
Remember, California is also where a questionable warrant was issued to seize a bloggers electronics, and then dropped, when Apple lost a prototype iPhone.
Remember, California is also where a questionable warrant was issued to seize a bloggers electronics, and then dropped, when Apple lost a prototype iPhone.
Thursday, May 19, 2011
Pattern Matching with iptables
iptables is the de facto linux firewall/packet filter. I just learned how to use pattern matching to filter unwanted HTTP requests.
Looking through apache logs, you'll see lots of people searching for vulnerabilities:
[error] [client 82.192.66.72] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
[error] [client 123.30.109.21] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
[error] [client 146.48.80.154] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
I am using fail2ban to watch the apache error logs and dynamically add iptables rules. I've had some success, but given that there are certain errors that: 1) I frequently see in the logs; 2) I know I should never see, I'm using the iptables pattern matching to filter the packet before it even hits Apache.
The technique is well documented here. The key line is :
Looking through apache logs, you'll see lots of people searching for vulnerabilities:
[error] [client 109.169.62.102] File does not exist: /var/www/database
[error] [client 199.71.213.70] File does not exist: /var/www/phpmyadmin
[error] [client 199.71.213.70] File does not exist: /var/www/phpMyAdmin
[error] [client 199.71.213.70] File does not exist: /var/www/PHPmyadmin
[error] [client 199.71.213.70] File does not exist: /var/www/pma
[error] [client 200.1.192.31] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:) [error] [client 199.71.213.70] File does not exist: /var/www/phpmyadmin
[error] [client 199.71.213.70] File does not exist: /var/www/phpMyAdmin
[error] [client 199.71.213.70] File does not exist: /var/www/PHPmyadmin
[error] [client 199.71.213.70] File does not exist: /var/www/pma
[error] [client 82.192.66.72] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
[error] [client 123.30.109.21] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
[error] [client 146.48.80.154] File does not exist: /var/www/w00tw00t.at.blackhats.romanian.anti-sec:)
I am using fail2ban to watch the apache error logs and dynamically add iptables rules. I've had some success, but given that there are certain errors that: 1) I frequently see in the logs; 2) I know I should never see, I'm using the iptables pattern matching to filter the packet before it even hits Apache.
The technique is well documented here. The key line is :
This will match an HTTP request for a file /w00tw00t.at.ISC.SANS. which is used in vulnerability scans. The above link goes into even more detail on how to specify which packets (eg- exclude connection requests (TCP SYN) packets)
# iptables -I INPUT -d xxx.xxx.xxx.xxx -p tcp \ --dport 80 -m string --to 70 --algo bm --string \ 'GET /w00tw00t.at.ISC.SANS.' -j DROP
Wednesday, May 18, 2011
Memristors: A fundamental shift in computing
Memristors are a new type of electronic component that is currently in development. They were theorized back in the 70s based on the fundamental properties of voltage, inductance, and capacitance. It makes the forth basic element to the existing resistor, capacitor, and inductor.
Memristors combine the function of transistor and memory, or to put another way, a logic circuit that remembers. This represents a tighter integration between processor and memory, much more so than just adding cache to a processor.
HP thinks memristors have a promising future in by [overcoming] the bottleneck of the Von Neumann architecture by integrating memory storage and data processing in a common circuit. Intel, however, seems to be following a more conventinoal approach to continue growth in computer power.
Memristors combine the function of transistor and memory, or to put another way, a logic circuit that remembers. This represents a tighter integration between processor and memory, much more so than just adding cache to a processor.
HP thinks memristors have a promising future in by [overcoming] the bottleneck of the Von Neumann architecture by integrating memory storage and data processing in a common circuit. Intel, however, seems to be following a more conventinoal approach to continue growth in computer power.
Tuesday, May 17, 2011
Interactive RF visualization
The Radio Frequency (RF) spectrum can be a confusing place to navigate. Running from a few kilohertz to man gigahertz, there's a lot packed in there. This is a great tool to help explore what various frequencies are used for.
New Fangled Lighting
Compact Florescent Lighting (CFL) has been touted as a major environmental improvement over inefficient incandescent. Problem is they contain mercury and improperly disposed are horrible for the environment. Solid State Lighting (SSL) based on Light Emitting Diodes (LEDs) are much more efficient but also much more expensive.
Having said that, I'm definitely sold on the wonderful world portrayed in this video:
GreenChip lighting lets you flip the switch remotely, thumbs nose at IPv4 depletion
Having said that, I'm definitely sold on the wonderful world portrayed in this video:
GreenChip lighting lets you flip the switch remotely, thumbs nose at IPv4 depletion
Subscribe to:
Comments (Atom)